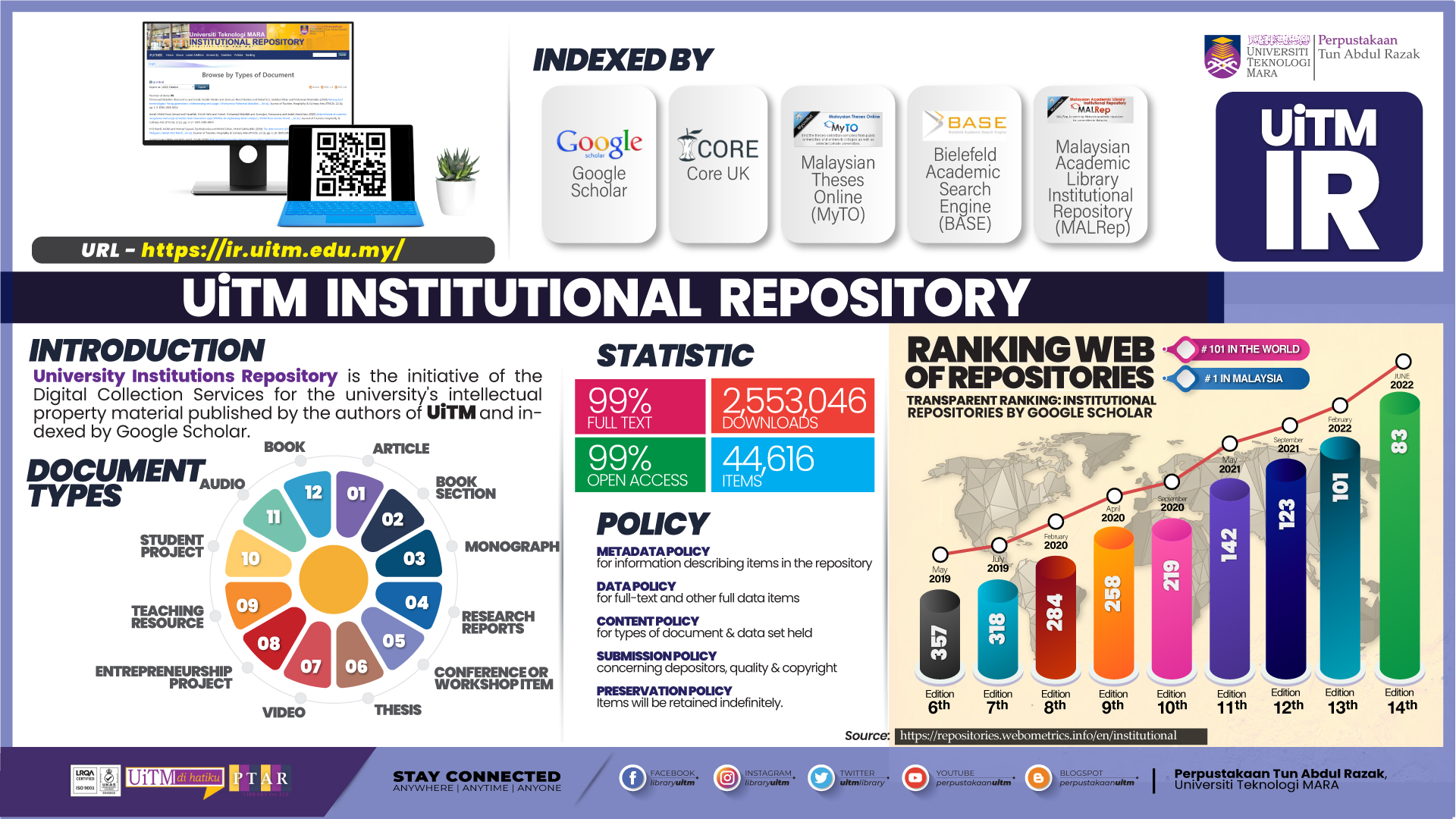
Most students never make it this far.
This is one of the sobering truths these librarians, representing a group of Illinois universities, have learned over the course of a two-year, five-campus ethnographic study examining how students view and use their campus libraries: students rarely ask librarians for help, even when they need it. The idea of a librarian as an academic expert who is available to talk about assignments and hold their hands through the research process is, in fact, foreign to most students. Those who even have the word “librarian” in their vocabularies often think library staff are only good for pointing to different sections of the stacks.
The ERIAL (Ethnographic Research in Illinois Academic Libraries) project -- a series of studies conducted at Illinois Wesleyan, DePaul University, and Northeastern Illinois University, and the University of Illinois’s Chicago and Springfield campuses -- was a meta-exercise for the librarians in practicing the sort of deep research they champion. Instead of relying on surveys, the libraries enlisted two anthropologists, along with their own staff members, to collect data using open-ended interviews and direct observation, among other methods.
The goal was to generate data that, rather than being statistically significant yet shallow, would provide deep, subjective accounts of what students, librarians and professors think of the library and each other at those five institutions. The resulting papers are scheduled to be published by the American Library Association this fall, under the title: “Libraries and Student Culture: What We Now Know.”
One thing the librarians now know is that their students' research habits are worse than they thought.
At Illinois Wesleyan University, “The majority of students -- of all levels -- exhibited significant difficulties that ranged across nearly every aspect of the search process,” according to researchers there. They tended to overuse Google and misuse scholarly databases. They preferred simple database searches to other methods of discovery, but generally exhibited “a lack of understanding of search logic” that often foiled their attempts to find good sources.
However, the researchers did not place the onus solely on students. Librarians and professors are also partially to blame for the gulf that has opened between students and the library employees who are supposed to help them, the ERIAL researchers say. Librarians tend to overestimate the research skills of some of their students, which can result in interactions that leave students feeling intimidated and alienated, say the ERIAL researchers. Some professors make similar assumptions, and fail to require that their students visit with a librarian before embarking on research projects. And both professors and librarians are liable to project an idealistic view of the research process onto students who often are not willing or able to fulfill it.
“If we quietly hope to convert all students to the liberal ideals of higher education, we may miss opportunities to connect with a pragmatic student body,” wrote Mary Thill, a humanities librarian at Northeastern Illinois. “… By financial necessity, many of today’s students have limited time to devote to their research.” Showing students the pool and then shoving them into the deep end is more likely to foster despair than self-reliance, Thill wrote. “Now more than ever, academic librarians should seek to ‘save time for the reader.’ ”
Before they can do that, of course, they will have to actually get students to ask for help. That means understanding why students are not asking for help and knowing what kind of help they need, say the librarians.
"This study has changed, profoundly, how I see my role at the university and my understanding of who our students are,” says Lynda Duke, an academic outreach librarian at Illinois Wesleyan. “It’s been life-changing, truly.”
Exploding the ‘Myth of the Digital Native’
The most alarming finding in the ERIAL studies was perhaps the most predictable: when it comes to finding and evaluating sources in the Internet age, students are downright lousy.
Only seven out of 30 students whom anthropologists observed at Illinois Wesleyan “conducted what a librarian might consider a reasonably well-executed search,” wrote Duke and Andrew Asher, an anthropologist at Bucknell University, whom the Illinois consortium called in to lead the project.
Throughout the interviews, students mentioned Google 115 times -- more than twice as many times as any other database. The prevalence of Google in student research is well-documented, but the Illinois researchers found something they did not expect: students were not very good at using Google. They were basically clueless about the logic underlying how the search engine organizes and displays its results. Consequently, the students did not know how to build a search that would return good sources. (For instance, limiting a search to news articles, or querying specific databases such as Google Book Search or Google Scholar.)
Duke and Asher said they were surprised by “the extent to which students appeared to lack even some of the most basic information literacy skills that we assumed they would have mastered in high school.” Even students who were high achievers in high school suffered from these deficiencies, Asher told Inside Higher Ed in an interview.
In other words: Today’s college students might have grown up with the language of the information age, but they do not necessarily know the grammar.
“I think it really exploded this myth of the ‘digital native,’ ” Asher said. “Just because you’ve grown up searching things in Google doesn’t mean you know how to use Google as a good research tool.”
Even when students turned to more scholarly resources, that did not necessarily solve the problem. Many seemed confused about where in the constellation of library databases they should turn to locate sources for their particular research topic: Half wound up using databases a librarian “would most likely never recommend for their topic.” For example, “Students regularly used JSTOR to try to find current research on a topic, not realizing that JSTOR does not provide access to the most recently published articles,” Duke and Asher wrote in their paper, noting that “articles typically appear in JSTOR after 3-5 years, depending on their publisher.” (JSTOR was the second-most frequently alluded-to database in student interviews, with 55 mentions.)
Years of conditioning on Google had not endowed the Illinois Wesleyan students with any searching savvy to speak of, but rather had instilled them with a stunted understanding of how to finely tune a search in order to home in on usable sources, concluded the ERIAL researchers.
Regardless of the advanced-search capabilities of the database they were querying, “Students generally treated all search boxes as the equivalent of a Google search box, and searched ‘Google-style,’ using the ‘any word anywhere’ keyword as a default,” they wrote. Out of the 30 students Duke and Asher observed doing research, 27 failed to narrow their search criteria at all when doing so would have turned up more helpful returns.
Unsurprisingly, students using this method got either too many search results or too few. Frequently, students would be so discouraged they would change their research topic to something more amenable to a simple search.
“Many students described experiences of anxiety and confusion when looking for resources -- an observation that seems to be widespread among students at the five institutions involved in this study,” Duke and Asher wrote.
These results can be taken in a positive light: as the library building has receded as a campus mecca, librarians have often had to combat the notion that online tools are making them irrelevant. The evidence from ERIAL lends weight to their counterargument: librarians are more relevant than they have ever been, since students need guides to shepherd them through the wilderness of the Web. Indeed, students who had attended library orientations or tutorials showed more proficiency than those who had not.
There was just one problem, Duke and Asher noted: “Students showed an almost complete lack of interest in seeking assistance from librarians during the search process.” Of all the students they observed -- many of whom struggled to find good sources, to the point of despair -- not one asked a librarian for help.
In a separate study of students at DePaul, Illinois-Chicago, and Northeastern Illinois, other ERIAL researchers deduced several possible reasons for this. The most basic was that students were just as unaware of the extent of their own information illiteracy as everyone else. "Some students did not identify that they were having difficulties with which they could use help," wrote anthropologist Susan Miller and Nancy Murillo, a library instruction coordinator at Northeastern Illinois. "Some overestimated their ability or knowledge."
Another possible reason was that students seek help from sources they know and trust, and they do not know librarians. Many do not even know what the librarians are there for. "I don't think I would see them and say, 'Well, this is my research, how can I do this and that?' " one senior psychology major told the researchers. "I don't see them that way. I see them more like, 'Where's the bathroom?' " Other students imagined librarians to have more research-oriented knowledge of the library but still thought of them as glorified ushers.
"Librarians are believed to do work unrelated to helping students," wrote Miller and Murillo, "or work that, while possibly related to research, does not entitle students to relationships with them."
Co-opting the influence of professors
In lieu of librarians, whose relationship to any given student is typically ill-defined, students seeking help often turn to a more logical source: the person who gave them the assignment -- and who, ultimately, will be grading their work. “[R]elationships with professors … determine students’ relationships with libraries,” wrote Miller and Murillo. "In the absence of an established structure ensuring that students build relationships with librarians throughout their college careers, professors play a critical role in brokering students' relationships with librarians," they wrote.
Because librarians hold little sway with students, they can do only so much to rehabilitate students’ habits. They need professors' help.
Unfortunately, professors are not necessarily any more knowledgeable about library resources than their students are. “Faculty may have low expectations for librarians, and consequently students may not be connected to librarians or see why working with librarians may be helpful,” wrote Miller and Murillo.
Several recent studies by the nonprofit Ithaka S+R have highlighted the disjunct between how professors view the library and how the library views itself: library directors see the library as serving primarily a teaching function; professors see it above all as a purchasing agent. Miller and Murillo heard echoes of that in their study. “I think that what happens is the librarians know how to search for sources, but sometimes don’t know how to do research,” one anthropology professor told them.
Professors are usually willing to try to put students on the right path. However, “a student will not necessarily succeed in research if he or she relies on the professor alone,” wrote Miller and Murillo. “… [Some] faculty members seemed to assume that students would pick up how to do library research, or that a one-shot instruction session, which at times professors erroneously assumed students previously had, would have been enough.”
This finding resonated with the librarians gathered here in Chicago. “Students do enough to get by,” says Lisa Wallis, a Web services librarian at Northeastern Illinois. “If they aren’t told to use [specific library] databases, they won’t.” And many professors, like many librarians, overestimate the research fluency of their students. For example, a professor might tell students to find “scholarly sources” without considering that students do not actually know what a “scholarly source” is, says Logan, the Chicago reference librarian.
At DePaul, “One of the professors said, ‘You mean they come to the library without the assignment?’ ” says Paula Dempsey, the coordinator of reference services there. “Yes. Yes, they do.”
Heather Jagman, a coordinator of library instruction at DePaul, described this as the “curse of prior knowledge” -- a phenomenon to which both professors and librarians are vulnerable. Teaching and library faculty are likely to have been exceptionally skilled researchers as undergraduates. Career academics might have a hard time putting themselves in the shoes of a student who walks into the library knowing practically nothing.
Pragmatism vs. Idealism
Part of the challenge for faculty in learning to serve students more effectively might be adjusting their expectations to the realities of what students already know -- and can be reasonably expected to learn -- in the space of a given assignment, says Thill, the humanities librarian at Northeastern Illinois.
In her contribution to the ERIAL tome, called “Pragmatism and Idealism in the Academic Library,” Thill wrote about the tension between library pragmatism -- the desire to satisfy the minimum requirements of a research assignment -- and library idealism, which glorifies the tedious unearthing and meticulous poring-over of texts. Unsurprisingly, most students tacked toward pragmatism, while “librarians and professors [repeatedly] wished that students could invest more time in contemplation and discovery, painting an idealized portrait of students leisurely wandering the stacks or pensively sitting down to await inspiration.”
Her findings, based on open-ended interviews with 30 faculty members and nine librarians at Northeastern Illinois and DePaul, pointed to the tension between the idealized view of academic research and the practical matters of deadlines and other limitations -- a tension librarians often have to resolve. If a student needs sources on a topic but does not know how to retrieve them, does the librarian find the source for him? Does she nudge him in the right direction but make sure he finds it himself? Librarians often have to walk that line between giving a person a fish and teaching her how to fish, proverbially speaking, says Thill. And the answer can rightly vary based on how quickly she needs a fish, whether she has the skills and coordination to competently wield a pole, and whether her ultimate goal is to become a master angler.
“Obviously I’m not saying we just have to be paper pushers -- just pushing out whatever it is the student wants,” Thill says. “But I think that, in general, we make decisions assuming that everyone is a career academic.”
This is treading on treacherous ground, and Thill knows it. The debate over whether librarians should be complicit in students’ efforts to “satisfice” -- that is, do what they can to get by and graduate -- can be a contentious one, since it runs to the root of what the library (and higher education in general) is for.
“To be honest I was almost afraid to write this paper,” she says, sitting in a conference room at the Northeastern Illinois library. “Whenever I talked to people about what my paper was about, they got their backs up.”
Thill says she does not think “satisfice” should be a dirty word. In her paper, she points to a 2008 NASPA Foundation study that indicated only 6 percent of college students earn a degree because they “like to learn for learning’s sake.” Back at the University of Illinois at Chicago, Logan mentioned the fact that a growing proportion of students are adult learners and first-generation students with jobs and family obligations. If these students are trying to “satisfice,” it probably isn't so that they'll have more time to goof off, she said.
There is also the somewhat dissonant fact that despite what the Illinois institutions now know about their students’ poor information literacy skills, many of those students have continued to pass their courses and eventually graduate. “I think we definitely saw that students are managing to get through without the level of certain research skills that we would like to see,” Asher told Inside Higher Ed.
“It’s not about teaching shortcuts, it’s about teaching them not to take the long way to a goal,” says Elisa Addlesperger, a reference and instruction librarian at DePaul. “They’re taking very long, circuitous routes to their goals.… I think it embitters them and makes them hate learning.” Teaching efficiency is not a compromise of librarianship, adds Jagman; it is a value.
Librarians and teaching faculty certainly have an obligation to encourage good, thorough research, says Thill, but they also have a responsibility to serve students -- and that means understanding the limitations of library idealism in practice, and acting pragmatically when necessary.